I have been intrigued by the capability of pfSense firewall for a while, but also been feeling intimidated by its “rumored” complexity for the initial set-up. The whole family is dependent on house wi-fi nowadays for almost everything they do except eating and sleeping (for the obvious reason). So, if I messed it up while replacing our reliable Asus RT-AC86U router with pfSense, I will be in deep trouble. 🙂
Therefore, I planned for about a month by having the right hardware ready, re-wired the computers and a few internet switches with ethernet cables, reading online articles, watching instruction youtube videos, and even trialed in a small, separate network, before I finally gained enough courage and took the plunge. I got up around 2 am last Saturday so that I could finish this home network transition before every other family members starts to complain (dad, my wi-fi isn’t working…), reconnected house network cables, connected the Fios ethernet cable directly to my pfSense box’ WAN port, then held my breath…
Everything worked (sigh) almost flawlessly – this is the reward of great planning! Except that kids and wife’s devices need to reset wi-fi password, there was essentially no internet down time for them; and they did not even necessarily know that I switched over to something entirely different, and reconfigured almost the entire house network – until two days ago my son realized that I suddenly gained the ability of cutting off his computer’s internet access after 5 pm each day (it’s just too much screen time for the kids nowadays while they get stuck in the house). 🙂
I spent the past a few days to fine-tune the home network. I tuned-up firewall rules, got home printers to work across different subnets, got port forwarding worked for the home server which serves this blog, set up openvpn, installed pfBlockerNG and all its related fine-tuning, and set up time restriction for my son’s laptops. Below is a documentation of what I have done. I want to do this because I know I will forget and because I hope my journey can help someone else with the same level of curiosity – pfSense can do that?!
Yes, it can – it is just that powerful.
First, I want to start with a diagram of my home network design.
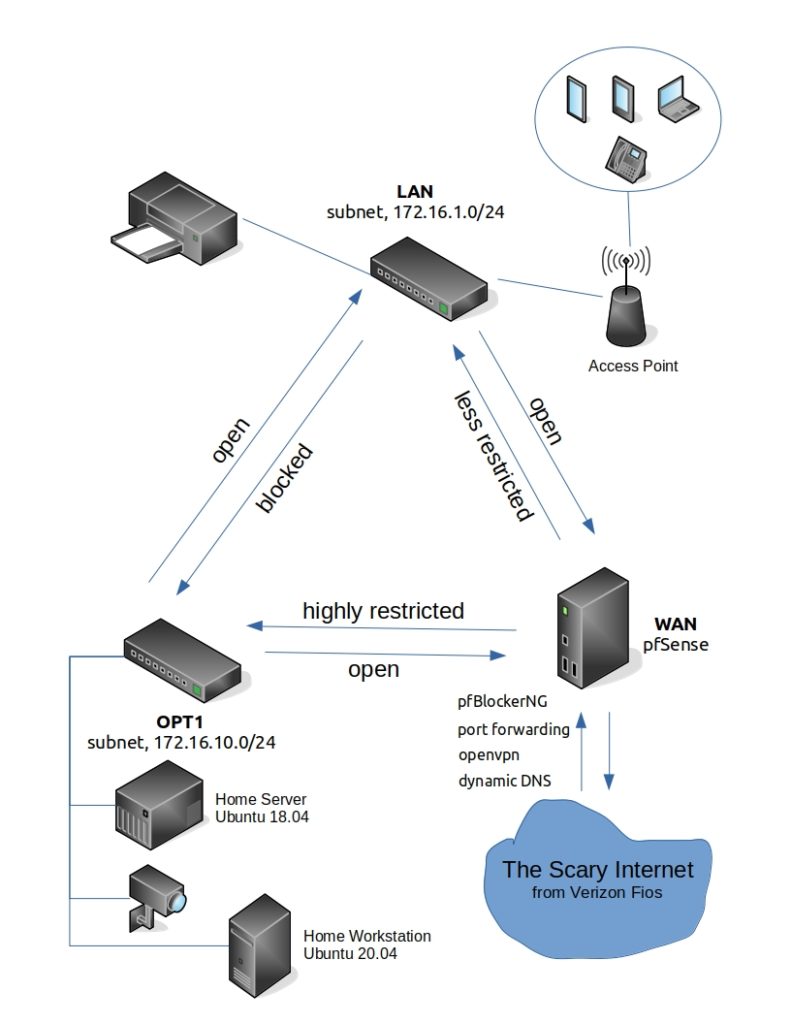
This design reflects a few priorities of mine for my home network:
- A robust firewall with a great flexibility of what I can do to the flow of internet into my house, which includes pfBlockerNG, port forwarding, dynamic DNS, and openvpn.
- A robust firewall with the great flexibility within my subnets so that I can isolate them into different zones: a more secure one (OPT1) that closed all ports except a few for server functions and blocks LAN access, and a less secure one (LAN) that allows OPT1 access and open ports with UPnP (so that the Xbox works :)).
- All mobile devices will be on LAN with a dedicated access point for wi-fi.
- Only wired devices are allowed on OPT1, including home security cameras (indoors and outdoors).
Now it’s time to talk about the “good stuff”.
- Hardware
Dell T20, Intel(R) Pentium(R) CPU G3220 @ 3.00GHz with 12 GB of RAM (this is over-kill by the way, but I have this server sitting in the basement and collecting dust. :))
Intel Pro 1000 PT Quad ethernet card (bought from ebay for $20, like this one)
TP-Link EAP245 access point. Can’t rate this little thing high enough. It is supper stable and covers my entire house without the need of a mesh network ($80-$100 on Amazon.com) - Installation
I can’t give enough credit to Lawrence Systems and his vlogs while I was setting up my own pfSense home firewall. My installation entirely followed his vlog, 2018 Getting started with pfsense 2.4 from install to secure! including multiple separate networks. I especially spurt out a great laughter to the first comment below his video: “This man is clearly doing God’s work.” – I can’t agree more! - Firewall rules for initial setup
WAN, port forwarding
LAN, anti-lockout, allow access within the same subnet, allow access to the internet, block access to OPT1 except ports for security cameras
OPT1, allow access within the same subnet, allow access to LAN, and allow access to the internet - Dynamic DNS
Google domain is your friend here. Adding a dynamic DNS in pfSense is most straightforward once you received the credential from Google Domain. - Path forward
As long as you know which ports you need to forward into your local network, this is most straightforward and no more difficult than what one needs to do on a regular consumer grade router. Here is the instruction.
Tip – What I found out, however, that I couldn’t access to my home WordPress server by only adding dynamic DNS and port forwarding. What’s missing is that I also needed to use DNS resolver (under Services), where everything else was kept default but only to add host override using my own domain name from Google Domain and my local server ip address. - OpenVPN
I simply followed this online instruction for openvpn. - pfBlockerNG
Here I went to get help from Lawrence Systems again and his great instructional video.
Tip – However, there are a few fine-tuning that I had to figure out by myself after the installation of pfBlockerNG. The first one is that to allow WeChat, one has to exclude China from being denied on GeoIP Top Spammers. The second is that to allow Ubuntu updates, one has to exclude UK from GeoIP Top Spammers.
Another interesting conversation during pfBlcokerNG set up was with my daughter. One evening, she rushed downstairs yelling at me, “Dad, my youtube videos are not working, and you set restricted mode on me!” The setting I used for that was the DNSBL SafeSearch feature. 🙂 - Time restriction on kids’ computers
Here I followed this great online video instruction.
Tip – However, when it was initially set up, the added firewall rules didn’t work until I had a hard reboot of the computer. It took me a long while to figure out what went wrong. It was because of my large number of pfBlockerNG rules, the default value for Firewall Maximum Table (40000) is not large enough anymore. After I gave a 2000000 value to this Firewall Maximum Table (System/Advanced/Firewall & NAT), everything worked like a charm!
My pfSense box is now rock solid and does exactly what I designed it to do. I can’t be happier! I will keep experimenting different features of this little beast and update on this blog what I have learned over time.
Feel free on the comment below, share with everyone your own journey with pfSense.